Our key areas of focus in design includes performance, resiliency, availability, convergence, growth and capacity planning, security integration and standardization.Our expertise spans across Datacenter/ISP Networks, Enterprise and Campus Networks.
There are three main phases involved and these are
- Requirements Analysis
- Network Audit
- Detailed Architecture Design
The requirements analysis phase is executed to ensure that all of the customers technical requirements are understood, clarified and documented. The requirements phase is normally conducted in a workshop environment with technical SMEs from relevant parties in attendance. Typical requirement discussions will include bandwidth, security, availability, architecture, protocol analysis and uptime requirements. The output and deliverables will include the production of:
- High level Solution Document (HLS)
- Customer Requirements Documents (CRD)
- Current state assessment Survey and Results (CSAS)
- Recorded Minutes and discussions for governance and traceability
If there is a requirement to upgrade an existing network, then the existing network is audited to baseline the hardware and Operating System and correlate this with existing inventory systems (if available) which allows us to determine the capabilities related to scalability, features and traffic profile.
The typical deliverables from this phase include:
- Network Audit Output.
- Updated CRD and HLS


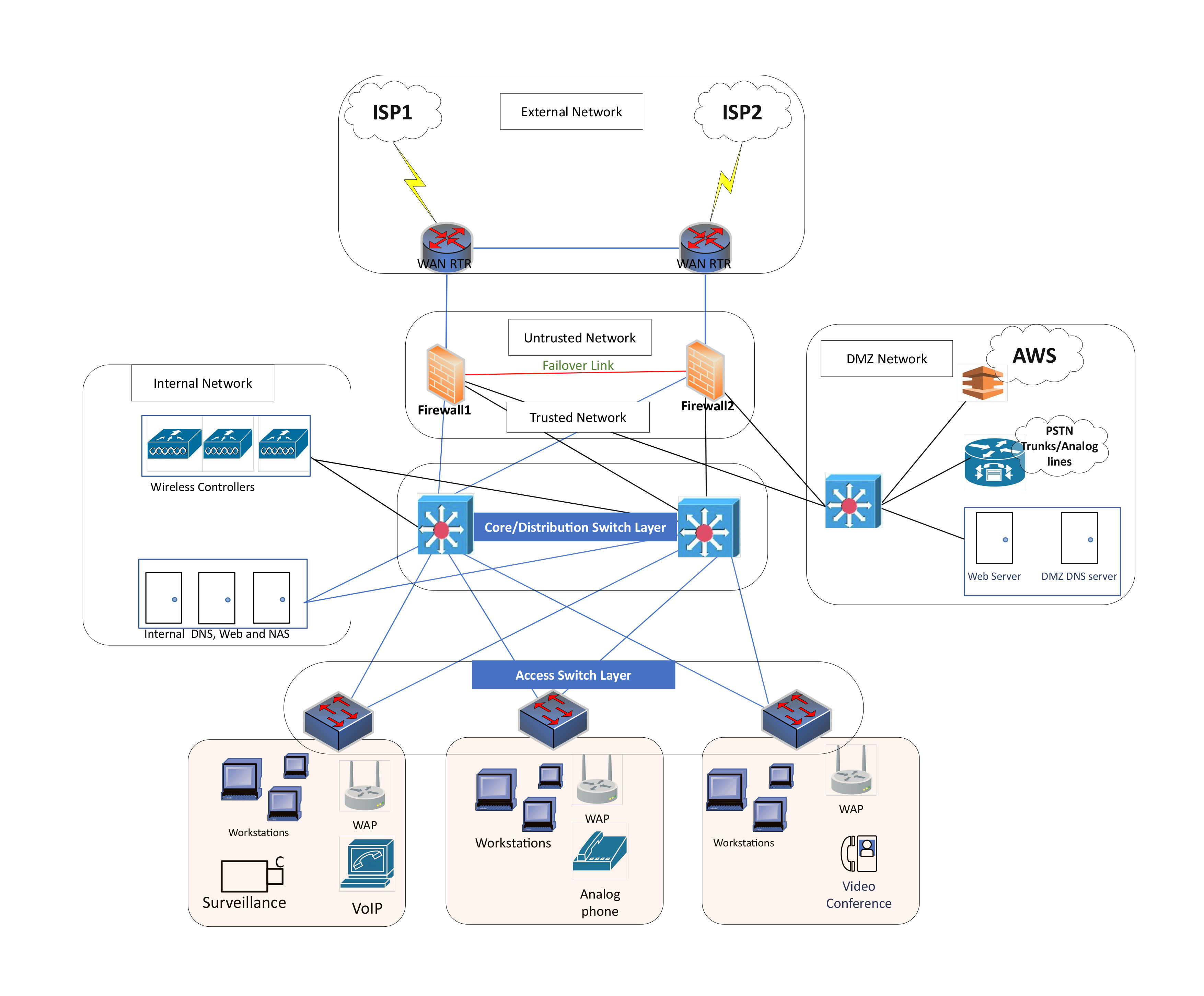
In this phase we will map the functions of the network into components. The physical and logical aspects of the network including hardware, protocols, media, will be defined. Any Cloud functions or requirements will also be considered. The Network Hierarchy is implemented normally segmented in to Core, Distribution and Access layers, which provides optimal network performance.
Each of the layers is responsible for handling relevant dataflows
- Core layer: Routes traffic between different geographical sites where high-throughput, low latency are the key requirements.
- Distribution layer: The distribution layer sits between the core and access layers, where network policies are applied to restrict or allow data flows between different distribution and edge layers within the network.
- Access layer: This layer is for the end device connectivity into the network via aggregation switches and will switch packets and route traffic. Access policy’s and access lists are also applied at this layer.The typical deliverables from this phase is.
- Low Level Design (Document, configs, parameters, etc.)
